the only package you need to install is the SSM Session Manager plugin for the AWS CLI
Install Session Manager plugin on Linux
check to see what is linux ARM 32 or 64 bit?
uname -m
download binary
curl "https://s3.amazonaws.com/session-manager-downloads/plugin/latest/linux_64bit/session-manager-plugin.rpm" -o "session-manager-plugin.rpm"yum install -y session-manager-plugin.rpmverify installation is successful


there is nothing you need to do because Fargate already includes all the infrastructure software requirements to enable this ECS capability


aws ecs update-service --cluster moti4-stage-cluster --service moti4-stage-cluster-MotibackendService-a4d1PuLnSkBd --enable-execute-command
An error occurred (InvalidParameterException) when calling the UpdateService operation: The service couldn’t be updated because a valid taskRoleArn is not being used. Specify a valid task role in your task definition and try again.
https://github.com/aws/aws-cli/issues/6242



{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssmmessages:CreateControlChannel",
"ssmmessages:CreateDataChannel",
"ssmmessages:OpenControlChannel",
"ssmmessages:OpenDataChannel"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogGroups"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:DescribeLogStreams",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:YOUR_REGION_HERE:YOUR_ACCOUNT_ID_HERE:log-group:/aws/ecs/CLUSTER_NAME:*"
}
]
}

region is the region where you created the cluster
us-east-1
get account id
aws sts get-caller-identity


Invalid ARN Account: The resource ARN account ID AIDAS47TNLLJGZDEPZWW4 is not valid. Provide a 12-digit account ID
I guess he meant the arn number






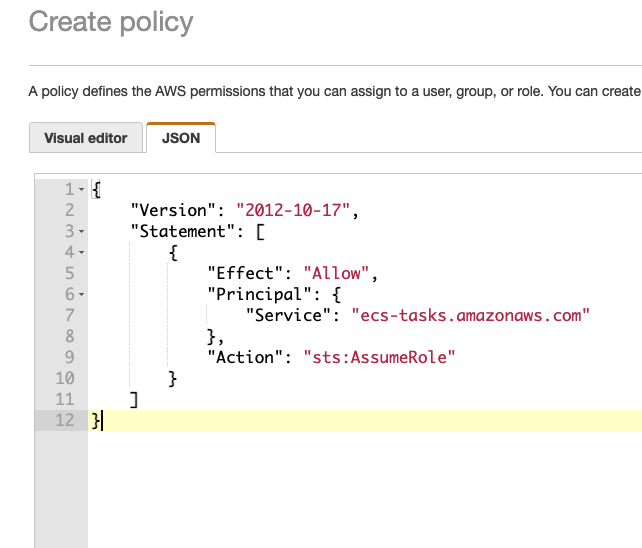
Now create role and add policy you just created







Create new Revision in ECS
https://docs.aws.amazon.com/AmazonECS/latest/developerguide/task-iam-roles.html

If you use the classic console to create your task definition, choose your IAM role in the Task Role field






aws ecs update-service --cluster moti4-stage-cluster --service moti4-stage-cluster-MotibackendService-a4d1PuLnSkBd --enable-execute-command --force-new-deployment
function get_task_arn {
aws ecs list-tasks --cluster moti4-stage-cluster --service moti4-stage-cluster-MotibackendService-a4d1PuLnSkBd --output text --query 'taskArns[0]'
}function ecs_exec {
local TASK_ARN=`get_task_arn`
aws ecs execute-command --cluster moti4-stage-cluster --task $TASK_ARN --container moti-backend --command "sh" --interactive
}